Our take on
Zero Trust Integration.
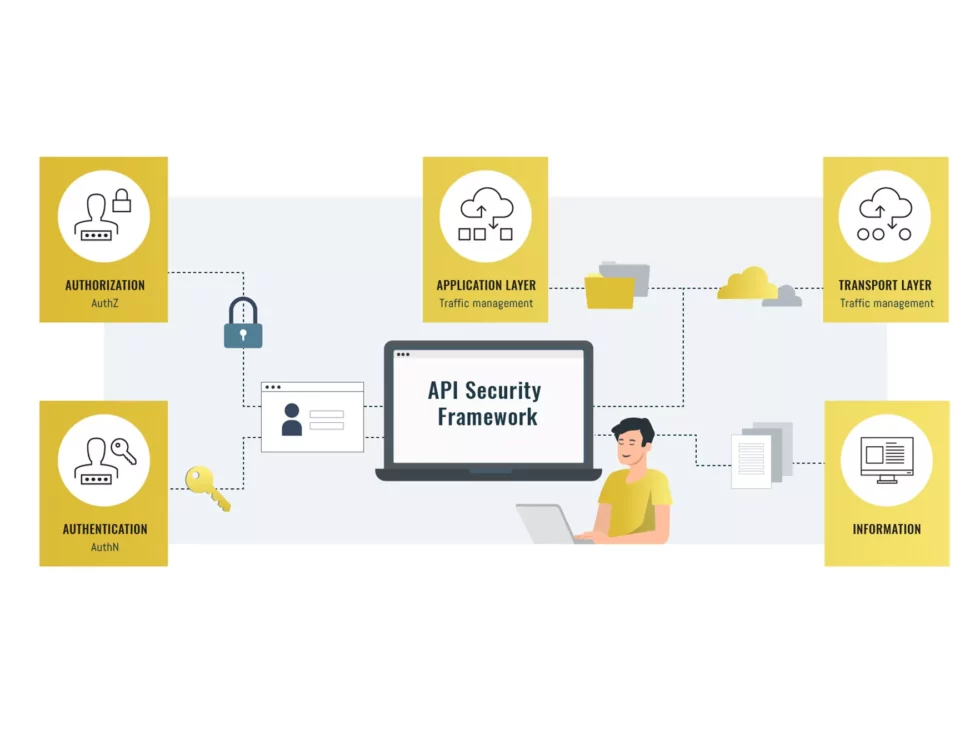
Zero Trust is not a technology. It’s a security mindset that ensures every integration between people, processes, and systems is verified, authorized, and monitored continuously.
We don’t build identity systems ourselves.
We design integrations that connect seamlessly to your existing IAM and governance processes for user management, verification, and policy enforcement.
That’s where Zero Trust integration truly begins.